Cybercrime , Cybercrime as-a-service , Finance & Banking
Russia's Cybercrime Rule Reminder: Never Hack Russians
BuyBest Bust: Russia Charges 25 Individuals With Trafficking in Stolen Bank Card Data
Reminder to Russian cybercriminals: Hit domestic targets at your peril.
See Also: Identity Security Clinic
Russian authorities typically turn a blind eye to cybercrime committed by citizens, provided they target foreigners - in part because the country's legal statutes have historically made such activity difficult to prosecute.
But authorities do not tolerate criminals that target Russians - and especially not anyone who targets Russian banks (see: Russian Cybercrime Rule No. 1: Don't Hack Russians).
Unfortunately for some domestic gangs, they don't appear to have gotten this message.

On Tuesday, Russia's Federal Security Service, known as the FSB, announced that together with Russia's Ministry of Internal Affairs, it had detained more than 30 individuals across 11 regions of the country - including Moscow, Crimea and St. Petersburg. Subsequently, authorities charged 25 of them with selling stolen credit and debit card that traced to Russian as well as foreign financial institutions.
Authorities have accused the individuals, who include Russian, Ukrainian and Lithuanian citizens, of creating more than 90 online stores to sell stolen data, as well as using the stolen card data to purchase and resell more than $1 million worth of goods. Authorities say that when they searched suspects' residences, they also seized firearms, illegal drugs, gold bars, precious coins, as well as cash: $1 million in U.S. dollars as well as 3 million rubles (worth $39,000).
The infrastructure being used by the alleged criminal enterprise has been shuttered, authorities say.
The FSB said one of the individuals it arrested had previously been jailed for similar offenses. That individual may be Alexey Stroganov, aka "Flint24," whose name has been posted to a LiveJournal blog together with a list of some of the other suspects and their court-appearance details. It says Stroganov was previously charged with carding offenses, received a six-year prison sentence in 2006 and was released in 2008.
Stroganov's arrest has also been confirmed by Moscow's General Judicial Court.
Likely: BuyBest/GoldenShop Disrupted
Russian authorities have not named the cybercrime marketplaces they shuttered.
But "around the same time as these arrests ... a popular dark web marketplace known as BuyBest, as well as its mirrors, went offline," says fraud intelligence firm Gemini Advisory in a blog post. "BuyBest is known for selling millions of compromised payment records, many of which include large amounts of personally identifiable information," and has been tied to GoldenShop.
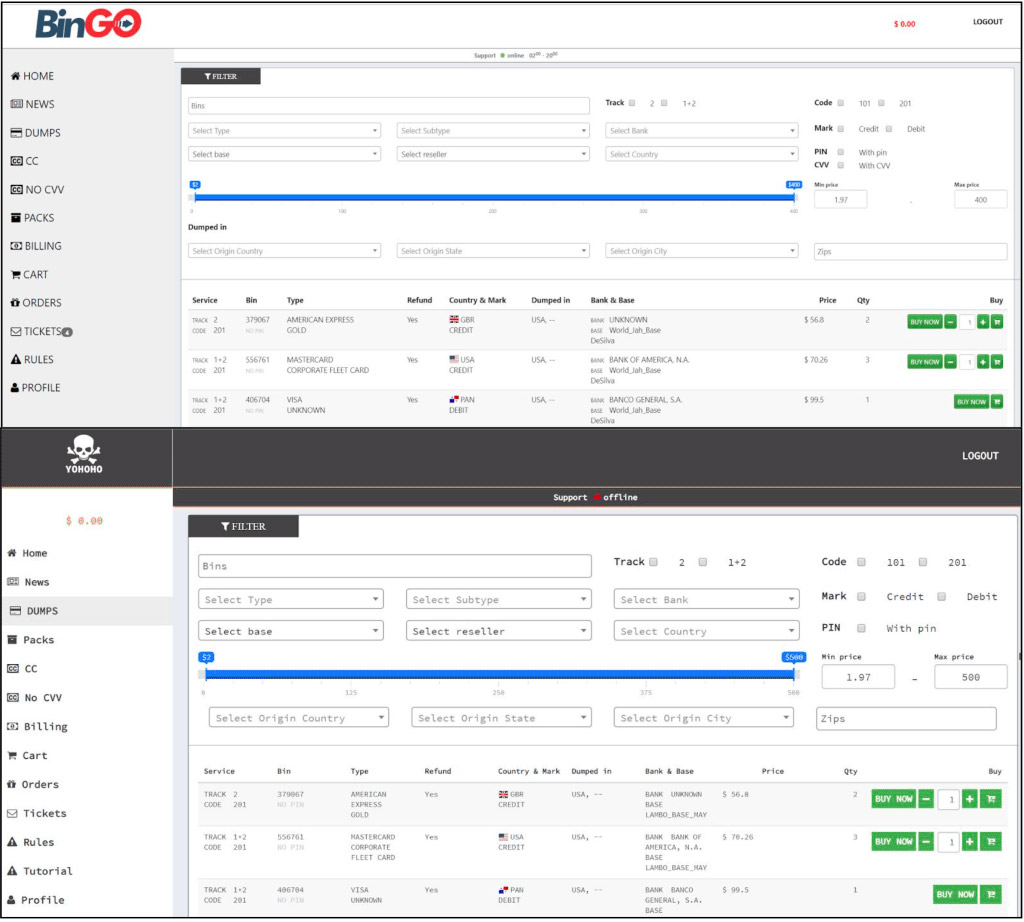
"BuyBest and GoldenShop are mirror markets, meaning that they sell compromised credit card information from the same sources and are oftentimes operated by the same groups of criminals," Gemini Advisory says. "This indicates that the hacker ring operated BuyBest and its mirrors, which have since been taken offline by Russian law enforcement."
Gemini Advisory says BuyBest first appeared in 2013, and estimates that the site led to profits of $18 million for the marketplace administrators, as well as $52 million in profits for the individuals who supplied the site with stolen card data.
"The marketplace was known for selling phished data, which often included Social Security numbers, dates of birth, victim IP addresses and [victims' browser] user agents. ... Some of the compromised records came from multi-location breaches at victim merchants such as Caribou Coffee and Russell Stover."
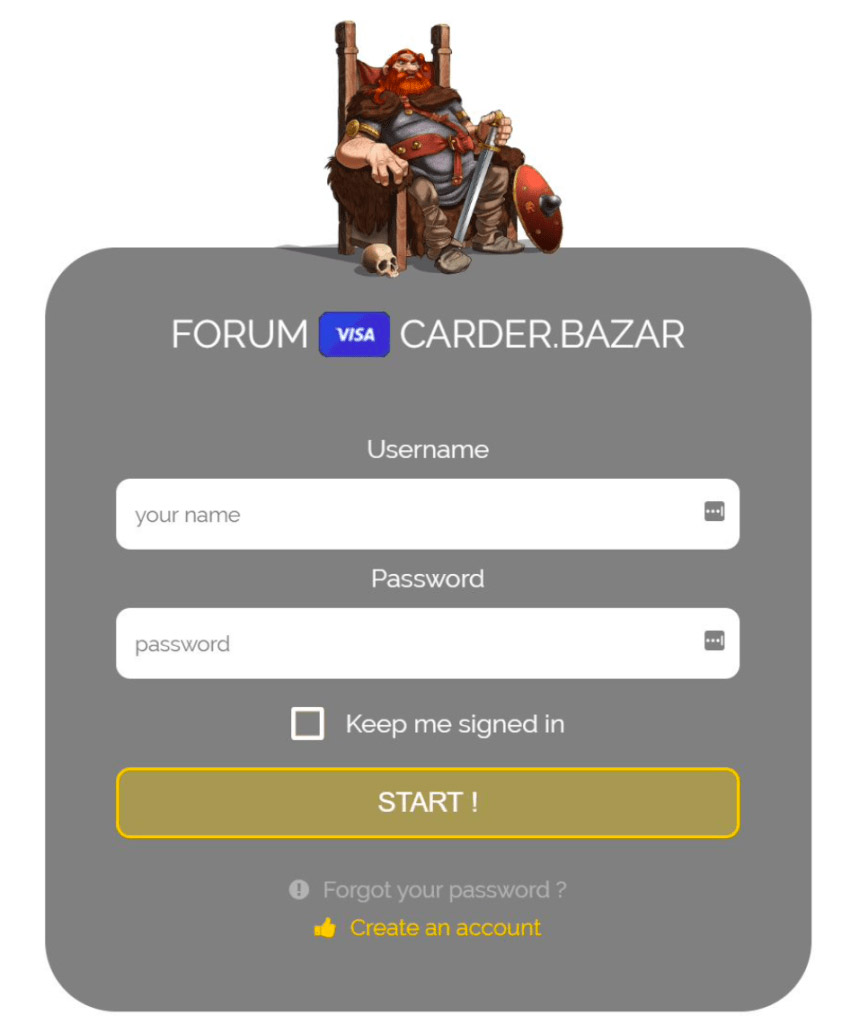
CarderBazar Forum
Unusually, BuyBest also featured its own, dedicated discussion forum.
"Most markets advertise their services in the general underground dark web forums, however, a select few run their own forum," Gemini Advisory says. "Marketplace administrators operated a forum called CarderBazar as a platform to advertise the GoldenShop/BuyBest and all of its mirrors, as well as to advertise the sales of new compromised card data. CarderBazar also had additional sections focusing on illegal cyber activities."
Flint24 and the larger group allegedly also ran such clear internet sites as wuzzup.com and dumpsmania24.com, as well as other sites that could only be accessed via the darknet - in other words, by using the anonymizing Tor browser, Cyberscoop reports.
Blocked: Selling Russian Cards
Gemini Advisory says that as is common with Russian language cybercrime forums, the BuyBest marketplace blocked the sale of payment cards issued by Russian banks. "It remains unclear if Stroganov and the other hackers targeted Russian businesses," the firm says. "If they did so, the data may have appeared on one of the over 90 purported mirrors, which could have drawn the attention of law enforcement."
Another possibility, it adds, is that the forum's administrators may have been set up by a rival. "Russian-language payment card marketplaces have engaged in aggressive sabotage before," it notes, pointing to sabotage conducted last year against the BriansClub dark web market, apparently by rivals who ran the Mr.Green marketplace.
Putin Orders Crackdown
The arrests also come as President Vladimir Putin has ordered the Ministry of Internal Affairs to crack down on internet-enabled crime, says Gary Warner, director of research in computer forensics at the University of Alabama in Birmingham.
In a speech earlier this month to Russia's parliament, the Duma, Putin said: "I'm asking for a system, a set of measures to reduce the number of such crimes."
Warner observes: "Guess what happens when President Putin orders the prosecutor general to do something to reduce the number of cybercrimes in Russia? The FSB gets to work arresting people."
Paunch's Downfall
The BuyBest arrests are unusual because at least historically, Russian authorities have rarely charged anyone with cybercrime offenses.
One notable exception occurred in October 2013, when authorities said they'd detained "Paunch," who was later named in numerous reports as being Dmitry E. Fedotov, then 27. At the time, security firm Group-IB, now based in Singapore, reported that Fedotov was the creator of the notorious Blackhole Exploit Kit, a crimeware-as-a-service offering available on a subscription-only basis for $500 per month; the Cool Exploit Kit; and the malware obfuscation service Crypt.am.

Shortly thereafter, the Ministry of Internal Affairs said the Blackhole cybercrime gang's activities had led to $2.1 million in fraud against Russian banks.
Takeaway: Russians who hack foreign targets face little risk of prosecution abroad because the Russian government doesn't extradite its citizens. But any Russians who choose to hack Mother Russia do so at their peril.











