Sponsored by Level 3
Sponsored by Level 3
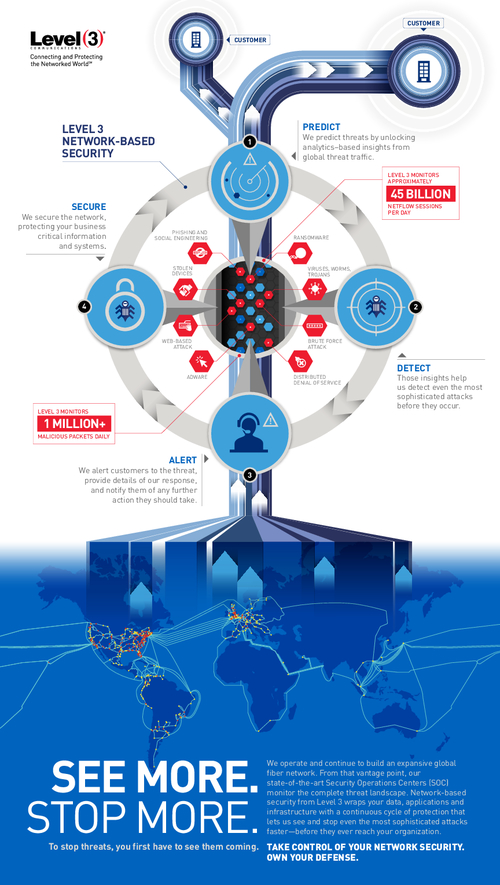
Improve Your Internet's Security
Sponsored by Level 3
Global Visibility: See More to Stop More (in German)
Sponsored by Intel
Defeat Ransomware: Ensure Your Data Is Not Taken Hostage
Sponsored by Intel
Safeguarding Against Pinkslipbot
Sponsored by Intel
McAfee Labs Threats Report June 2016
Sponsored by Intel
The Benefits of Endpoint Detection and Response
Sponsored by Pulse Secure
Pulse Policy Secure Solution Guide - Enhanced Firewall Security
Sponsored by PhishLabs
Security Awareness Training Buyer's Guide: Sharpening Human Defenses Against Phishing
Sponsored by Intel Security
Think Like an Attacker: Six Steps Toward Better Security
Sponsored by PhishLabs
The CISO's Guide to Spear Phishing Defense
Sponsored by IBM
Multi-Channel Banking Fraud
Sponsored by IBM